Basics of Wireless Communication for Sensors
Integral to the seamless operation of Wireless Sensor Networks (WSNs) is wireless communication, allowing sensors to transmit and receive information without the limitations of wired connections. A basic understanding of wireless communication is critical to designing and optimizing the performance of wireless sensors.

Figure 1: WSN Architecture
Modulation and Demodulation
Modulation: At the core of the process, modulation is a crucial technique that involves varying the properties of a carrier wave in accordance with the signal to be transmitted. Based on the system needs and transmission conditions, different modulation schemes such as Frequency Modulation (FM), Amplitude Modulation (AM), and Phase Modulation (PM) are used. For the transmission of binary information, digital modulation techniques like Quadrature Amplitude Modulation (QAM) and Phase Shift Keying (PSK) are frequently employed.
Demodulation: The procedure of extracting the original data from the modulated carrier wave once it reaches the receiver is demodulation, the converse of modulation. The demodulation technique chosen depends on the modulation scheme employed. Ensuring accurate synchronization of the modulation and demodulation processes is imperative to prevent any loss of information.
Power Considerations for Wireless Sensors
Power Constraints: Operating on constrained power sources such as batteries or energy harvesters, wireless sensors require careful power management to extend the lifespan of the sensors. In remote and inaccessible areas where replacing power sources is impractical, efficient power usage is pivotal in sustaining communication, and sensor operation.
Power Management Techniques: To reduce energy consumption, power-conscious design techniques like adaptive transmission power and duty cycling are used. Optimizing energy utilization involves programming sensors to enter low-power states when not actively engaged in transmitting or receiving data.
Energy-Efficient Communication: Power consumption is impacted by the choice of modulation and signal processing methods. Crucial to the sustainability of a wireless sensor network is the selection of energy-efficient communication methods, thereby extending the functional life of wireless sensors.
Exploring the fundamentals of wireless communication reveals the intricate arrangement of modulation and demodulation methods, which are crucial for the transmission of information in Wireless Sensor Networks (WSNs). In navigating the realm of wireless sensors, it is indispensable to be mindful of power considerations. This involves meticulous management and conservation of energy resources to guarantee both longevity and reliability of the sensors. A solid groundwork for robust and efficient wireless sensor networks is established through the synergy of adept communication techniques and careful power management. This synergy propels advancements across various applications, spanning from environmental monitoring to healthcare.
Network Topologies
Network topology defines the architecture of interconnections between the nodes in a Wireless Sensor Network (WSN). The communication manner of nodes is outlined by the topology, thereby impacting the network’s robustness, adaptability, and energy efficiency. The three primary common topologies in WSNs are mesh, star, and hybrid. All of them offer unique benefits and challenges.
Star Topology
A central coordinator or a gateway is present in the star topology with which all other sensor nodes are connected directly giving it the shape of a star. This coordinator usually acts as the point of connection to other networks, and it is also responsible for handling the communication within the network.
Advantages
- Simplicity and Ease of Implementation: The set up and management becomes easier with the straightforward design.
- Centralized Control: Efficient management and network control is enabled by the central coordinator.
Disadvantages
- Single Point of Failure: A vulnerability is introduced through the central coordinator, as its failure could render the entire network incapacitated. Scalability Issues: As the number of connected nodes increases, the scalability of the network may be restricted, leading to potential degradation in performance.
Mesh Topology
A web-like structure where each node is connected to various other nodes is mesh topology. The utilization of multiple interconnections allows data to navigate diverse paths, ensuring its arrival at the destination even in the event of node failures.
Advantages
- Robustness and Reliability: The network’s resilience to node or connection failures can be enhanced by the presence of numerous paths.
- Enhanced Range: By hopping between intermediate nodes, data can travel longer distances.
Disadvantages
- Complexity: More advanced algorithms and protocols are needed to manage complicated connections and routing data in mesh networks.
- Higher Energy Consumption: Quicker depletion of energy resources is the result of the increased count of connections and constant communication between nodes.
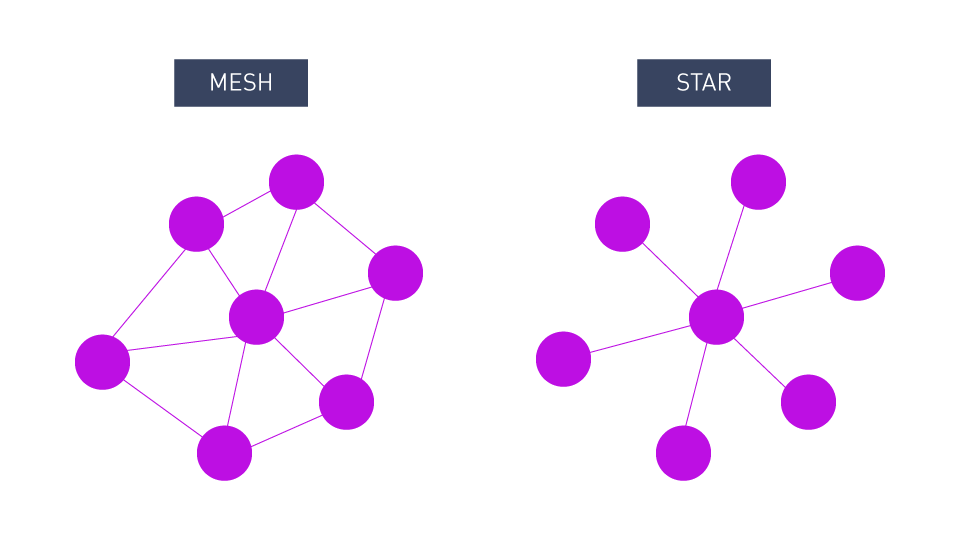
Figure 2: Star vs. Mesh Topology
Hybrid Topology
Combining the features of various topologies forms a hybrid network topology, strategically harnessing the advantages of each while simultaneously aiming to mitigate their respective disadvantages. For example, blending the simplicity of a star topology with the reliability of a mesh topology creates a hybrid network that incorporates the strengths of both.
Advantages
- Flexibility and Adaptability: According to particular needs and constraints, it enables the optimization of the network.
- Balanced Performance: Balanced Performance can provide a perfect trade-off between reliability, energy efficiency and ease of management.
Disadvantages
- Design Complexity: Creating a complex yet effective hybrid topology necessitates careful planning and design.
- Management Overhead: To manage the different connections and data paths effectively, the combination of various topologies may introduce extra management overhead.
The foundation of WSNs, network topologies impact their efficiency, flexibility, and dependability. Depending on the particular needs and limitations of the application, one may choose between star, mesh, or hybrid topologies, each of which has advantages and disadvantages of its own. For the purpose of developing and optimizing WSNs for a variety of applications, including smart cities and environmental monitoring, a thorough understanding of these topologies is necessary.
Protocols and Standards
Strong and effective communication protocols and standards are essential for Wireless Sensor Networks (WSNs) in order to promote security, interoperability, and efficient data transfer among various sensor nodes and systems. A number of well-known protocols and standards, including as Bluetooth Low Energy (BLE), LoRa, and Zigbee, are especially designed to meet the special needs of WSNs.
Zigbee
A set of high-level communication protocols using low-power digital radios is outlined in the Zigbee specification. Due to its low power consumption, mesh networking compatibility, and capacity for several nodes, it is especially well suited for WSNs.
Advantages
- Low Power Consumption: On limited battery resources, it allows longer lifespan of network.
- Mesh Networking: Through multi-loop communication, it enhances network range.
- High Scalability: With thousands of nodes, it supports large networks.
Applications
- Home Automation: Due to its low power need and reliability, Zigbee is popular in smart home devices.
- Industrial Automation: Zigbee is majorly used to monitor and handle industrial settings.
LoRa
A patented digital wireless data communication method is called Long Range (LoRa). Small amounts of data may be transmitted over long distances with it, which makes it a great option for remote sensor networks in difficult conditions.
Advantages
- Long Range: With minimal energy consumption, it offers communication over long distances, usually several kilometers.
- Low Power: For remote and inaccessible sensor nodes, it enables extended battery life.
Applications
- Agriculture: LoRa is widely used in agriculture to monitor soil moisture, temperature, and other aspects.
- Environmental Monitoring: To monitor environmental conditions, it is ideal for implementing sensors in remote areas.
Bluetooth Low Energy (BLE)
BLE is a low-power version of the traditional Bluetooth protocol that is intended for close-quarters device connection. It works best in applications where minimal energy consumption is essential and minimal data transfer is needed.
Advantages
- Low Energy Consumption: Prolongs battery-powered devices' operational life by offering connectivity options.
- Ubiquity: Its broad support across a range of devices promotes ease of integration and interoperability.
Applications
- Healthcare: In order to transfer data to smartphones or other devices, wearable health monitoring gadgets frequently use BLE.
- Retail: Facilitates the delivery of information and proximity-based services in retail settings.
The proper protocols and standards must be chosen in order for WSNs to be deployed effectively. While BLE is synonymous with short-range, low-energy communication, LoRa focuses on long-range, low-power data transfer, while Zigbee is well known for its scalability and support for mesh networking. When creating WSNs, it is important to take into account the unique needs and limitations of the intended application, as each has unique benefits and appropriate application domains.
Remote Sensing and Real-Time Monitoring
Wireless Sensor Networks (WSNs) are essential for real-time monitoring and remote sensing because they allow data to be collected, processed, and sent from a variety of environmental characteristics. This talk explores the fundamentals of data gathering, aggregation, and transmission methods that are critical to real-time monitoring and distant sensing in wireless sensor networks (WSNs).
Data Collection
Remote sensing begins with data collection, which is the process of using various sensors to measure and identify physical characteristics, environmental factors, or changes in the environment. The data is then transformed into a form that can be understood, usually an electrical signal.
Analog-to-Digital Conversion
Sensor data is initially processed digitally by means of analog to digital conversion. Sampling, quantization, and encoding are only a few of the steps that are involved.
- Sampling: Involves deciding on particular intervals or spots to measure and record data for.
- Quantization: Producing discrete values from the continuous sampled signals.
- Coding: Requires using a digital code to represent discrete quantities.
Digital signals are converted from analog to digital using an analog-to-digital converter (ADC).
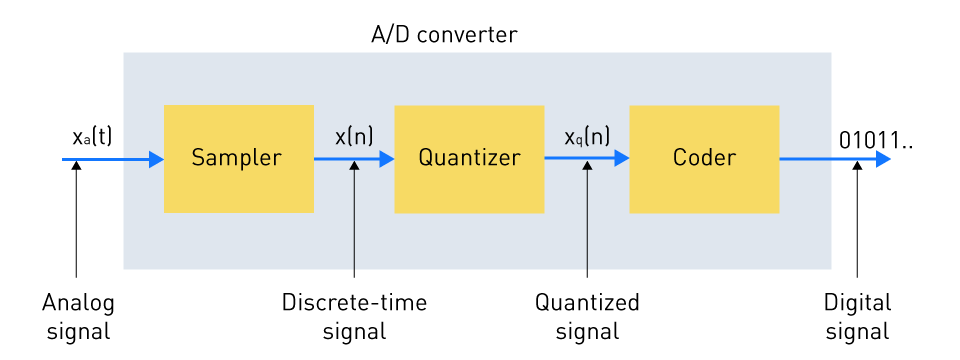
Figure 3: Basic Components of an Analog-to-Digital Converter (ADC)
Considerations
- Sensitivity: Minimal changes in the measured parameters must be detected by sensors with skill.
- Accuracy: A realistic picture of the real environmental circumstances must be included in the data that is gathered.
Data Aggregation
One important step in reducing redundancy and increasing data transmission efficiency is data aggregation, which is the act of combining and processing the acquired data. In order to make more thorough and precise deductions, it entails combining data from several sensors.
Techniques
- Averaging: By averaging several readings, it lowers noise and increases accuracy.
- Min/Max: Finding extreme numbers facilitates the identification of abnormalities or crucial circumstances.
Considerations
- Latency: In order to preserve the relevance of the data, there should be as little delay as possible while processing and aggregation.
- Resolution: After aggregation, the degree of detail kept should match the needs of the application.
Data Transmission
The procedure ends with the aggregated data being transmitted to the base station or cloud for additional analysis and action. For the data to be precisely and quickly received at its destination, effective data transmission is essential.
Techniques
- Modulation: Data is transmitted over the communication channel by being embedded into carrier waves.
- Channel Coding: Introducing extra bits that aid in locating and fixing transmission faults brought on by interference and noise.
Considerations
- Bandwidth: To handle the volume of transferred data, adequate bandwidth is required.
- Reliability: Maintaining the integrity of the data requires ensuring error-free transmission.
In wireless sensor networks, real-time monitoring and remote sensing depend on careful data collection, transmission, and aggregation. When these processes are strategically implemented, accurate and significant data is communicated in real time, which promotes prompt and knowledgeable decision-making. Adequacy of these procedures is critical to the design and deployment of WSNs since it directly affects the overall sensor network's efficiency and dependability.
Energy Harvesting for WSNs
Energy harvesting and conservation become crucial in these isolated and difficult-to-reach places where Wireless Sensor Networks (WSNs) are frequently installed. In order to lessen reliance on batteries and maintain the longevity and sustainability of the sensor network, energy-harvesting technologies seek to collect and store ambient energy from the surrounding environment. This section clarifies the concepts and uses of solar, vibrational, and radiofrequency energy harvesting in wireless sensor networks (WSNs).
Solar Energy Harvesting
In order to provide sensors in well-lit areas with a sustainable and renewable energy source, solar energy harvesting uses photovoltaic cells to transform sunlight into electrical energy.
Principles:
- Photovoltaic Effect: The process by which a substance exposed to light produces a voltage or electric current.
Applications: Ideal for outdoor applications where sunlight is plentiful, such as meteorological and agricultural sensors.
Challenges: It depends on the presence of sunlight, thus, it is not always present in dimly lit areas or at night.
Vibrational Energy Harvesting
Using piezoelectric or electromagnetic transducers, vibrational energy harvesting harnesses the mechanical vibrations found in the environment to produce electrical energy.
Principles:
- Piezoelectric Effect: Electric charge generated by mechanical stress conversion.
Applications: Suitable for industrial environments such as transportation systems or manufacturing factories where machinery produces continuous vibrations.
Challenges: Generally speaking, the energy yield is minimal and depends on the vibrations' frequency and amplitude.
RF Energy Harvesting
By converting ambient radio frequency signals into DC power, RF energy harvesting captures energy from these signals and can be helpful in low-power applications and situations when alternative energy sources are limited.
Principles:
- Rectification: Producing direct current (DC) from alternating current (AC) generated by radio waves.
Applications: Ideal for cities with a high concentration of radio frequency (RF) signals from broadcast stations, Wi-Fi, and mobile networks.
Challenges: The conversion efficiency is frequently low, and thus necessitates a powerful and steady RF source.
The sustainability of Wireless Sensor Networks is contingent upon the utilization of energy harvesting technology, particularly in remote and inaccessible deployments. Solar energy harvesting works best in areas with lots of sunlight, however consistency is a problem. While it works well in industrial environments, vibrational energy collecting often produces little energy. In cities with lots of RF signals, RF energy harvesting is common, but it requires a steady supply and good conversion efficiency. The environment and energy requirements of the sensor network must be considered when choosing an energy collecting strategy.
Security and Privacy in WSNs
Given the sensitivity and importance of the data they handle, Wireless Sensor Networks (WSNs) must provide security and privacy. This section explores the processes that protect user privacy and strengthen WSNs against hostile activity, such as intrusion detection, trust establishment, and data encryption.
Data Encryption
A crucial element in preserving the integrity and secrecy of data transferred over WSNs is data encryption.
Principles: Using cryptographic keys and techniques, data encryption hides information from prying eyes by converting plain text into encrypted text.
Methods:
- Symmetric Encryption: The same key is used for encryption and decryption. Efficiency is achieved, but vulnerability arises in case of key compromise.
- Asymmetric Encryption: Enhanced security comes through the utilization of a key pair, consisting of both public and private keys; however, this improvement is accompanied by an augmented computational load.
Challenges: Maintaining a crucial equilibrium between the level of security and the computational overhead is essential, particularly when dealing with resource-constrained sensor nodes.
Trust Establishment
In collaborative and decentralized networks such as WSNs, the trust establishment allows sensor nodes to validate the authenticity of their peers—a critical aspect for seamless operation.
Principles: Based on past interactions and feedback from other nodes in the network, trust models typically assess the behavior and dependability of nodes.
Applications: Crucial for preventing malicious nodes from compromising the network through attacks or spreading false data.
Challenges: The creation of trust models that are both robust and adaptive is essential. These models must withstand sophisticated attacks while accurately evaluating the trustworthiness of nodes.
Intrusion Detection
To monitor and detect malicious activities within the network, intrusion detection systems (IDS) are used. It helps in timely identification and risk mitigation.
Principles: To identify malicious activities, IDS typically utilize specification-based, signature-based, or anomaly-based detection methods.
Implementation: The combination of local and global detection strategies is used by effective IDS to ensure complete coverage and precise anomaly detection.
Challenges: Balancing the attainment of high detection accuracy with the minimization of false positives and negatives poses a challenge, necessitating ongoing refinement and adaptation of Intrusion Detection Systems (IDS).
Carefulness and multilayered techniques are required for security and privacy in WSNs. Both of them are complicated yet inseparable elements. To handle resource constraints, data encryption demands optimized algorithms and safeguard information against unauthorized access. To precisely assess node behavior, trust establishment is critical in keeping network integrity and requires advanced models. Essential for timely identification and mitigation of threats, intrusion detection requires a seamless integration of diverse methodologies for effective operation. Fundamental to unlocking their complete potential across diverse application domains is the assurance of resilient and secure operation in Wireless Sensor Networks (WSNs).







直接登录
创建新帐号